How to monitor Asterisk
There are three main ways to monitor Asterisk.
Choose the method that suits your environment.
CLI (Command Line Interface)
Execute Asterisk CLI commands from zabbix-agent for monitoring.
Format the return value with grep or awk to make it into a form of data that can be imported into ZABBIX.
SNMP (Simple Network Management Protocol)
SNMP (Simple Network Management Protocol) is used.
You need to have Net-SNMP installed and Asterisk ready to use SNMP.
AMI (Asterisk Manager Interface)
Originally, telnet 5038 is used, but Asterisk has a built-in HTTP/HTTPS server, so it is possible to use AMI via HTTP/HTTPS.
Use AMI over HTTP(S)
The official site zabbix.com has a page for monitoring Asterisk using AMI over HTTP(S).
https://www.zabbix.com/integrations/asterisk
There is also a list of available data.
README.md
ZABBIX6.0
https://git.zabbix.com/projects/ZBX/repos/zabbix/browse/templates/tel/asterisk_http?at=release/6.0
ZABBIX5.4
https://git.zabbix.com/projects/ZBX/repos/zabbix/browse/templates/tel/asterisk_http?at=release/5.4
You should enable the mini-HTTP Server, add the option webenabled=yes in the general section of the manager.conf file and create Asterisk Manager user with system and command write permissions within your Asterisk instance.
Create an AMI user with webenabled=yes in the general section of manager.conf with system privileges and write privileges.
Create an AMI user
Official:sample of manager.conf
https://github.com/asterisk/asterisk/blob/master/configs/samples/manager.conf.sample
Setting for HTTP
Default is HTTP. You can also support HTTPS if you set http.conf as above.
An example of using 8088 for HTTP and 10089 for HTTPS.
Official:sample of http.conf
https://github.com/asterisk/asterisk/blob/master/configs/samples/http.conf.sample
Setting for Firewall
Allow communication from ZABBIX server on TCP5038 (AMI) TCP8088 (HTTP).
When using HTTPS, open TCP10089 in the above example.
Check using AMI from browser via HTTP
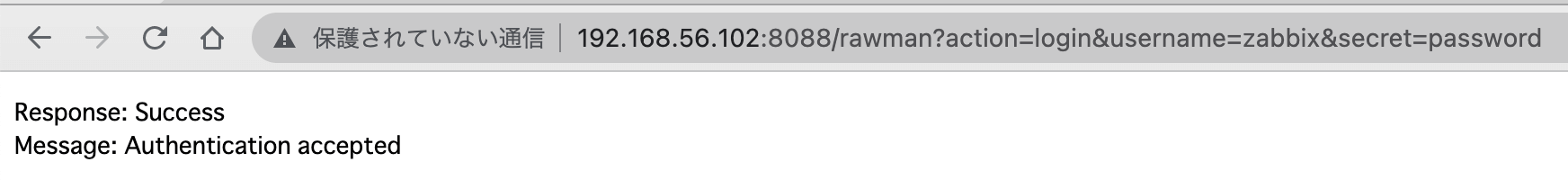
Login:
http://<IP>:8088/rawman?action=login&username=zabbix&secret=password
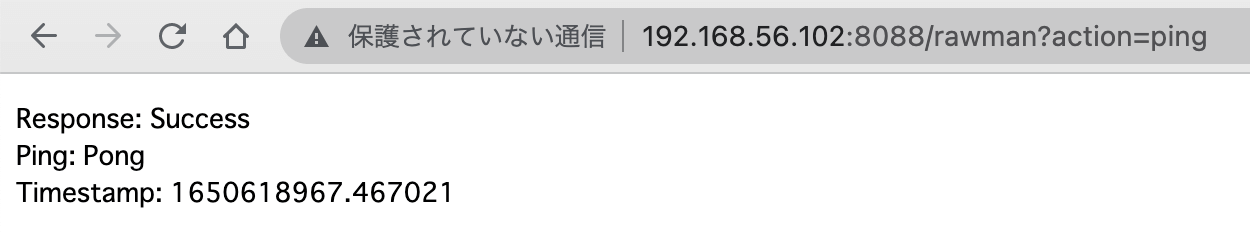
Check for response:
http://<IP>:8088/rawman?action=ping
Import template to ZABBIX server
Download template_tel_asterisk_http.yaml and import it to ZABBIX server.
Assign templates to hosts and set macros
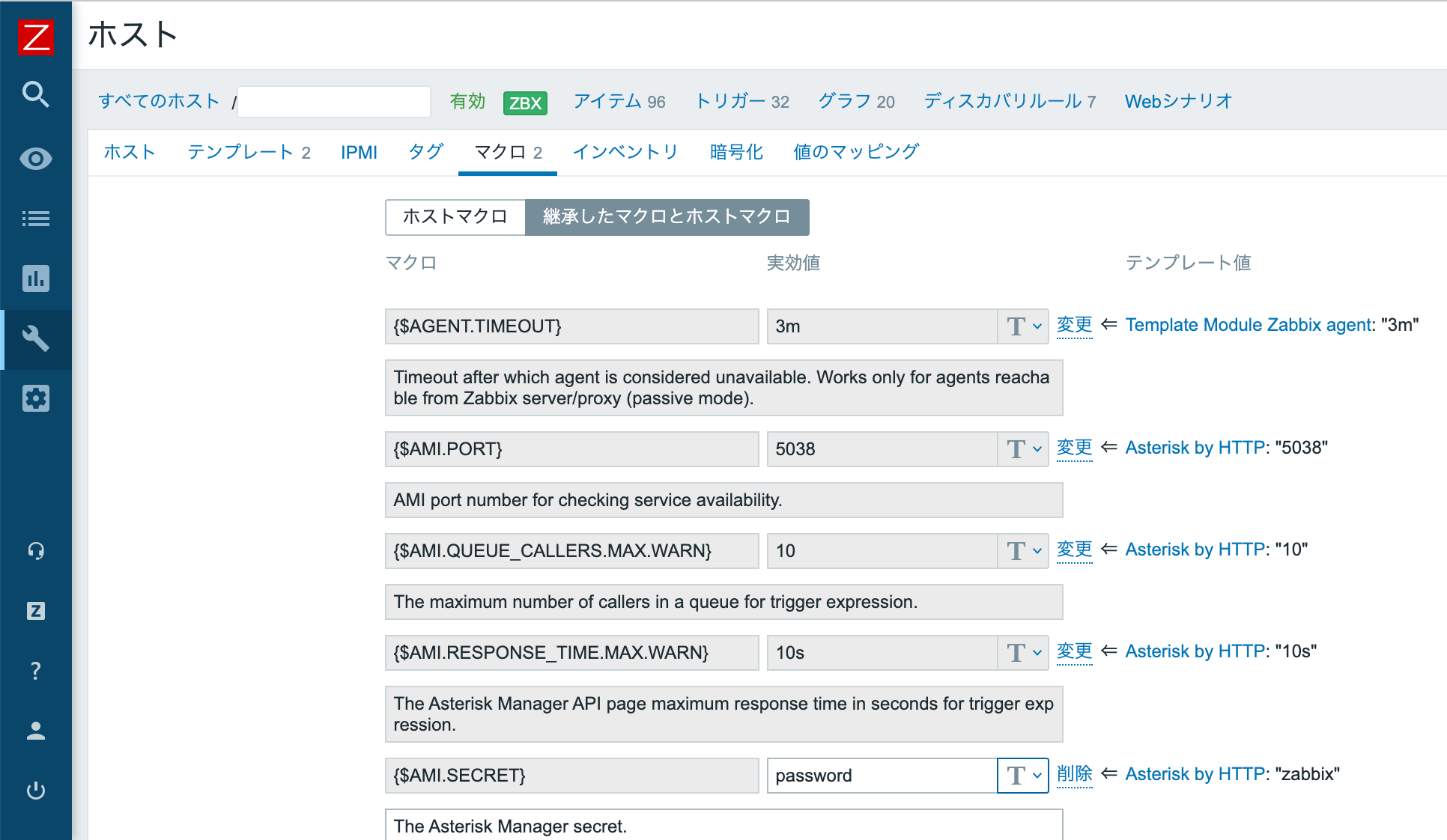
Assign templates to monitored hosts.
Change the macro.
- {$AMI.SECRET} set password
- {$AMI.URL} http(s)://<IP or FQDN>:8088/rawman
The template default AMI.URL is http://asterisk:8088/asterisk/rawman, but this is the case when prefix=asterisk is set in http.conf, so specify :8088/rawman.
Check data
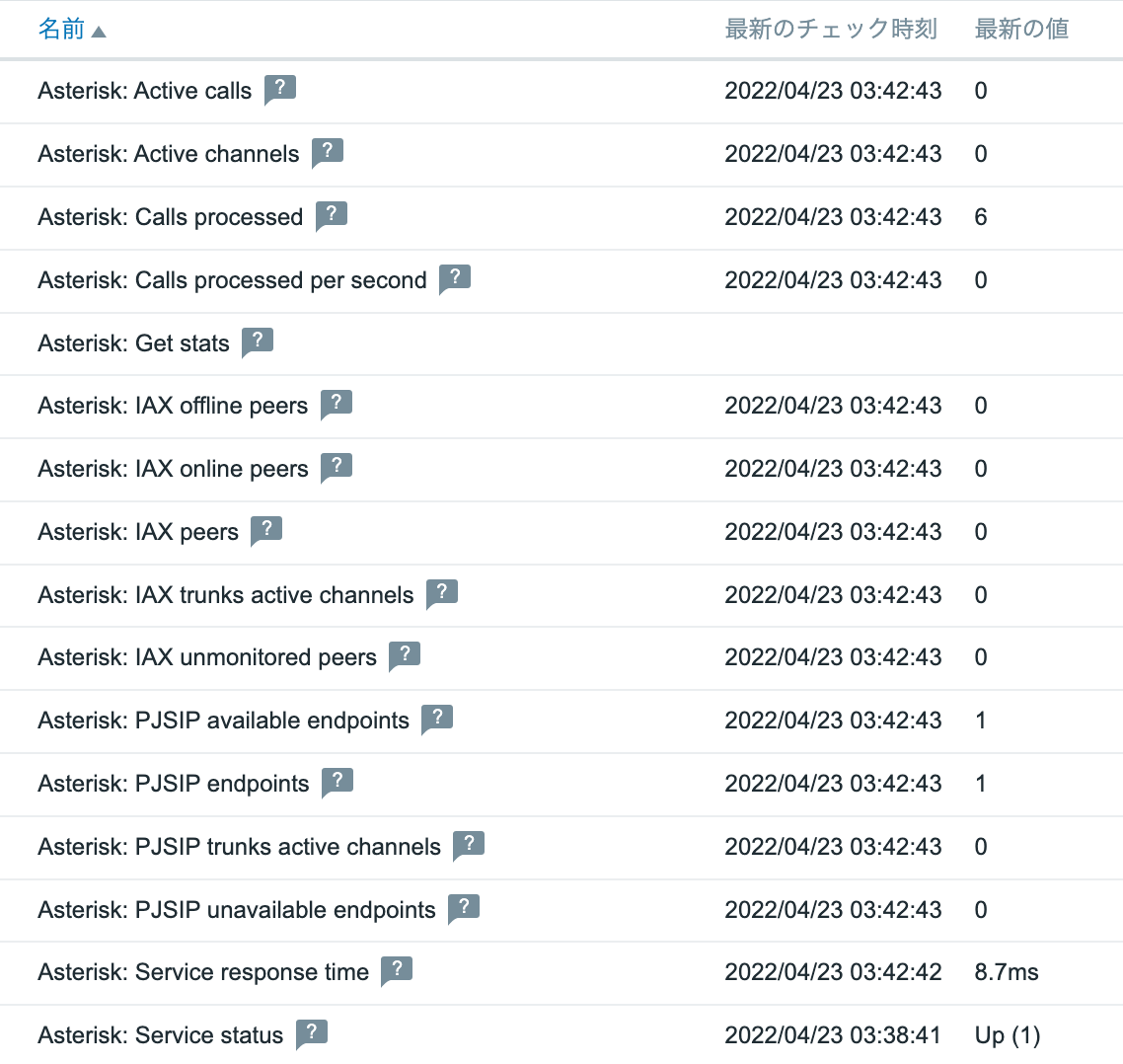
How to monitoring
ZABBIX official Asterisk by HTTP template obtains call volume information such as active calls via AMI via HTTP(S).
The original AMI of TCP5038 is used for Asterisk’s life and death monitoring and response speed monitoring.
Since we are only checking whether there is a TCP connection response without authentication, an authentication error will be output to the log on the Asterisk side, but there is no problem.