See encrypted SIP packets
IP-PBX that communicates with SIP may use UDP or may be encrypted with TCP/TLS.
If it’s encrypted, you can’t see it with Wireshark.
It is possible to visualize (decrypt) the encrypted SIP by obtaining the private key from the SIP server and loading it into Wireshark.
Useful for troubleshooting, etc.
You can also check SIP/TLS from the browser using Homer introduced below.
Get private key
For Asterisk, it is in /etc/asterisk/keys/asterisk.key like this.
Import key to Wireshark
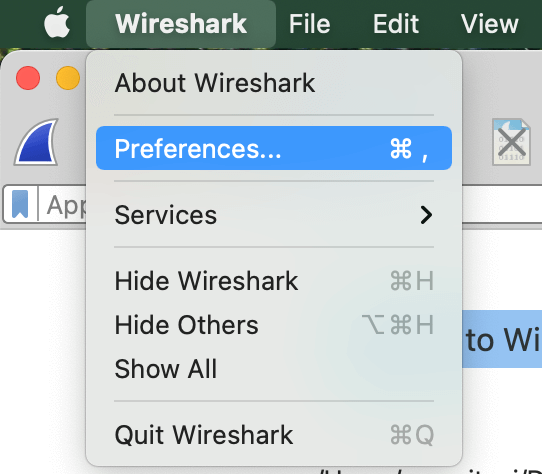
Wireshark > Preferences…
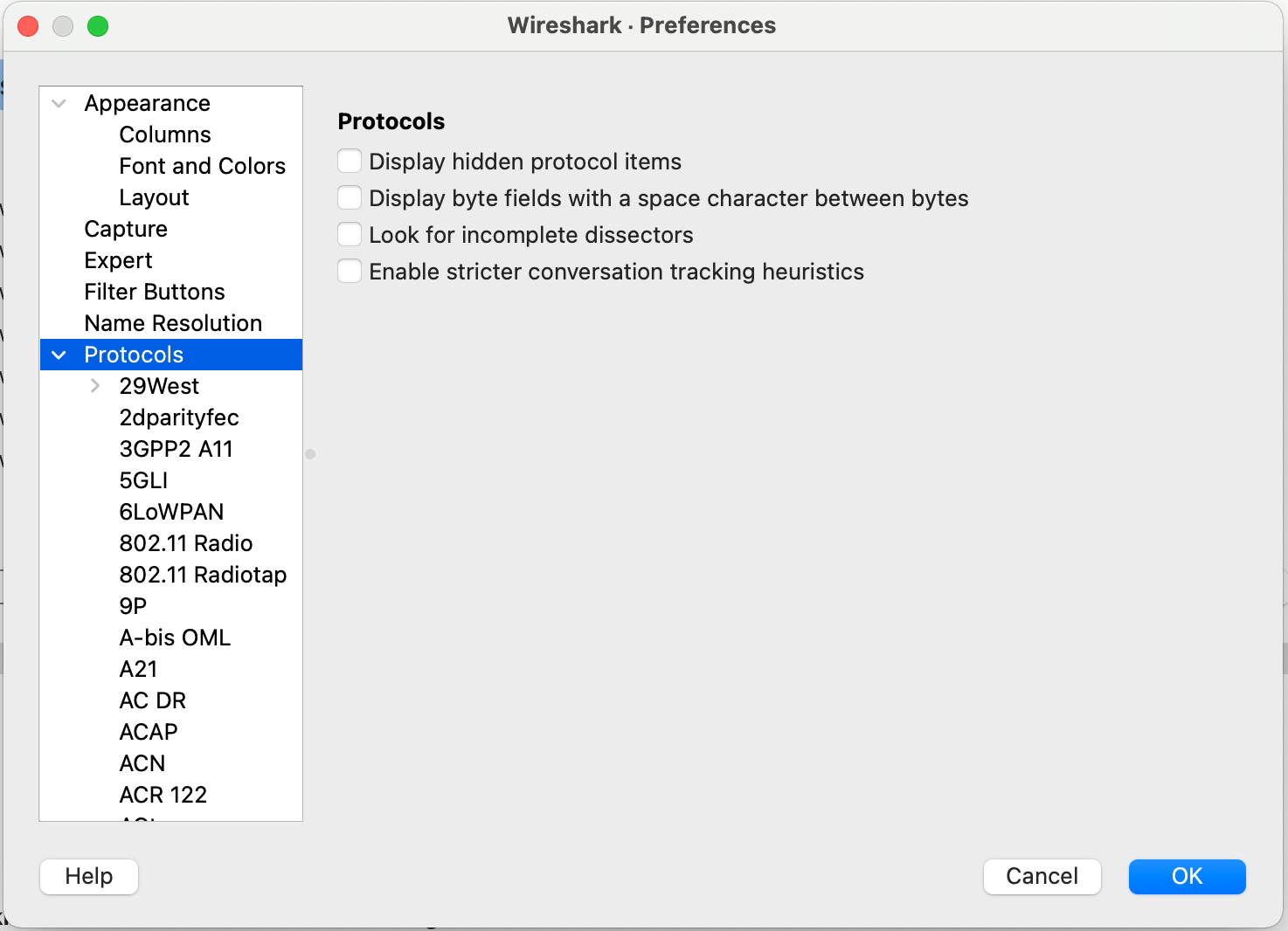
Protocols >
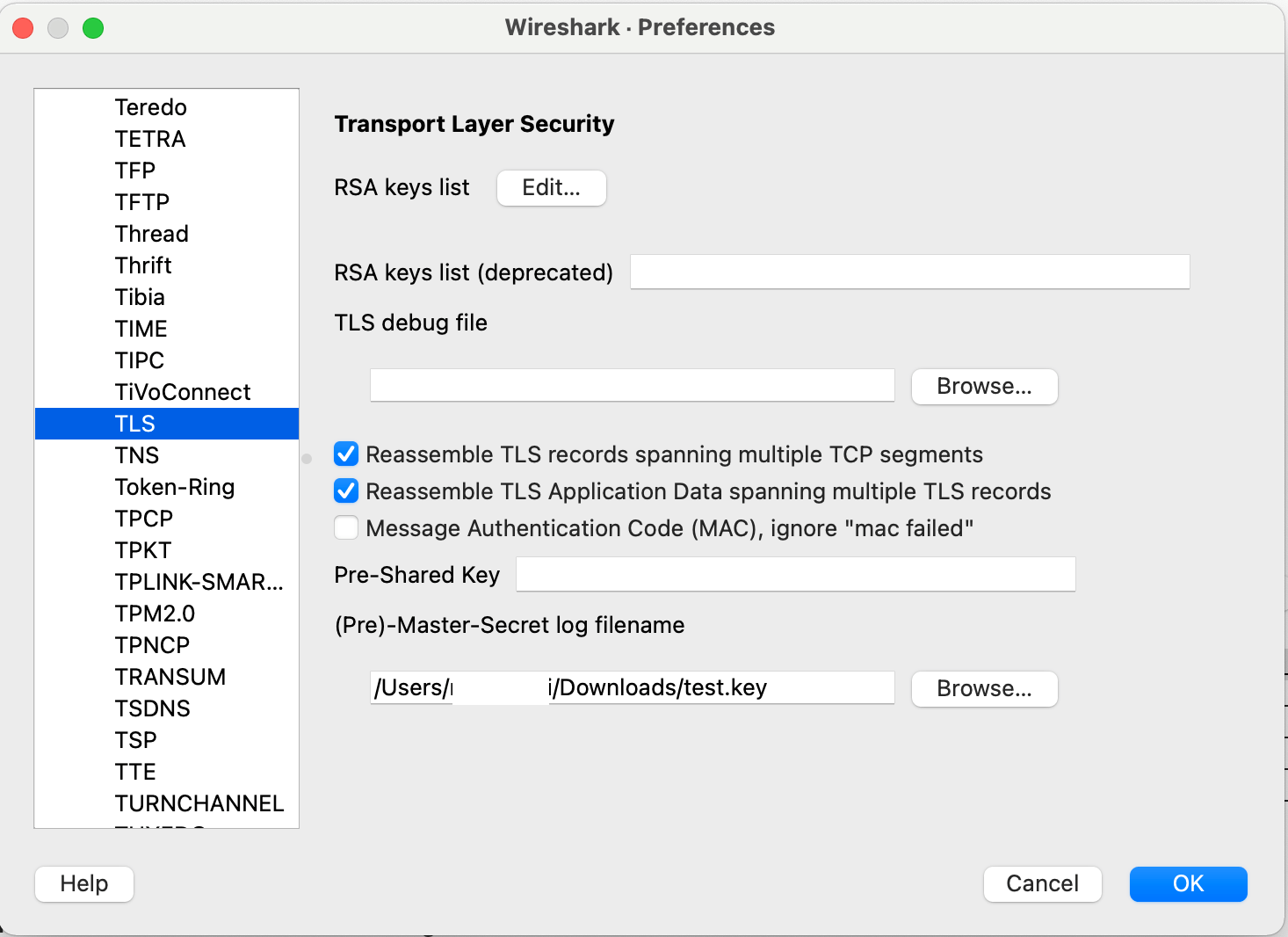
Protocols > TLS > (Pre)-Master-Secret log filename
Set for private key.
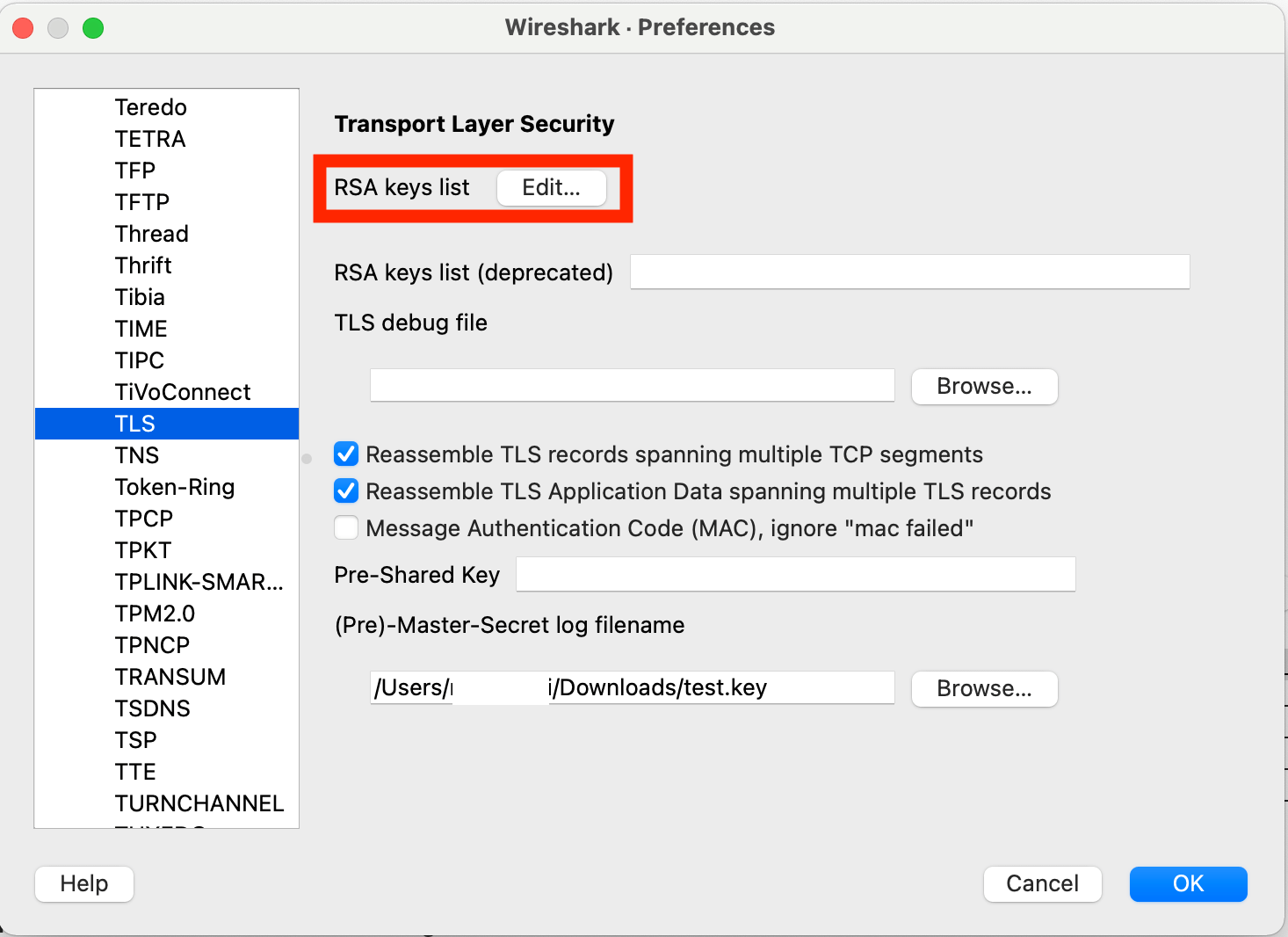
Click for RSA keys list.
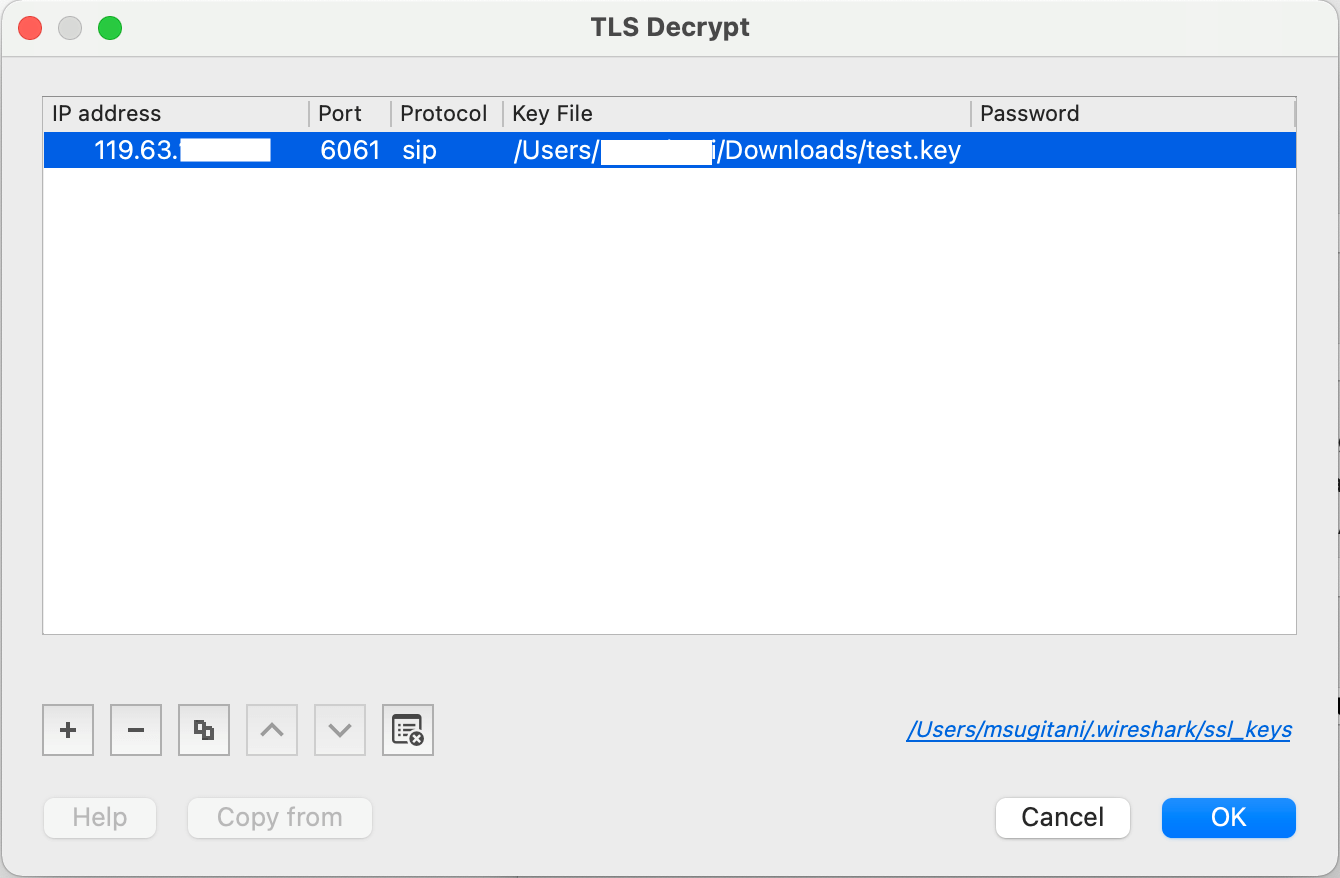
Click + and then add items as below.
・IP address :
・Port :
・Protocol : sip
・Key File : specify private key
See decoded SIP packets
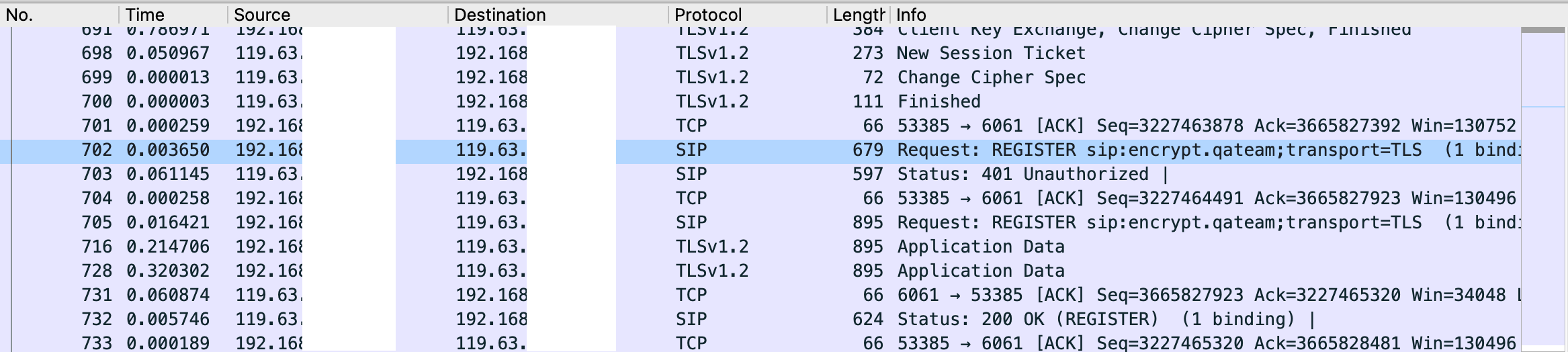
The protocol that was TLSv1.2 before decryption is displayed as SIP.
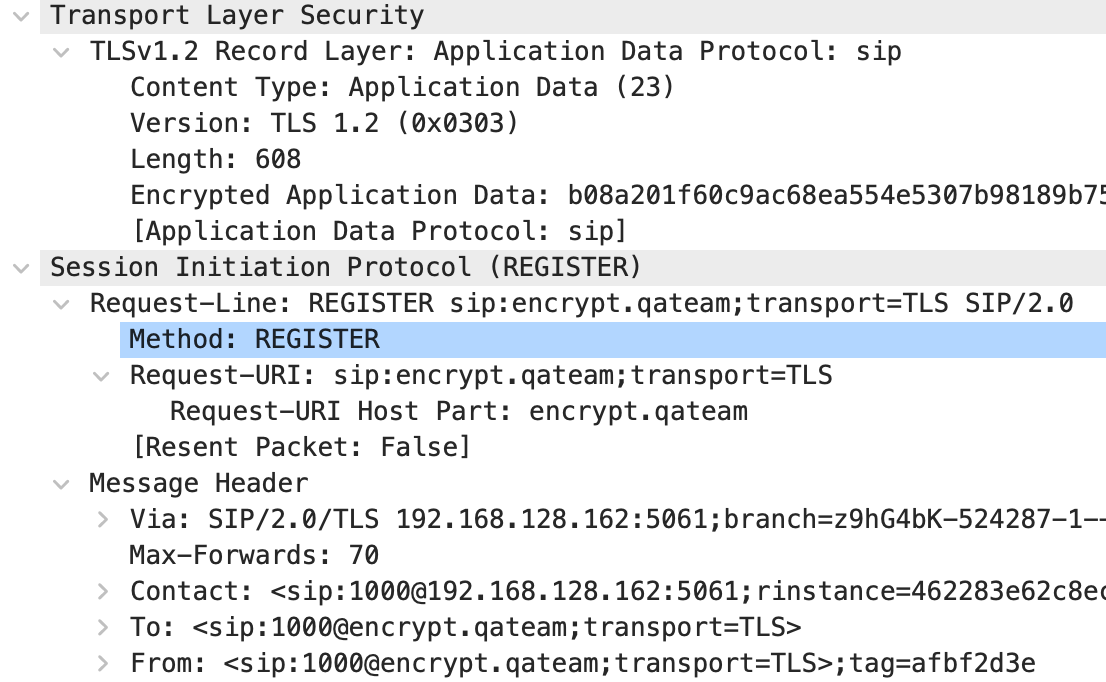
A SIP REGISTER decrypted from TLSv1.2 is displayed.
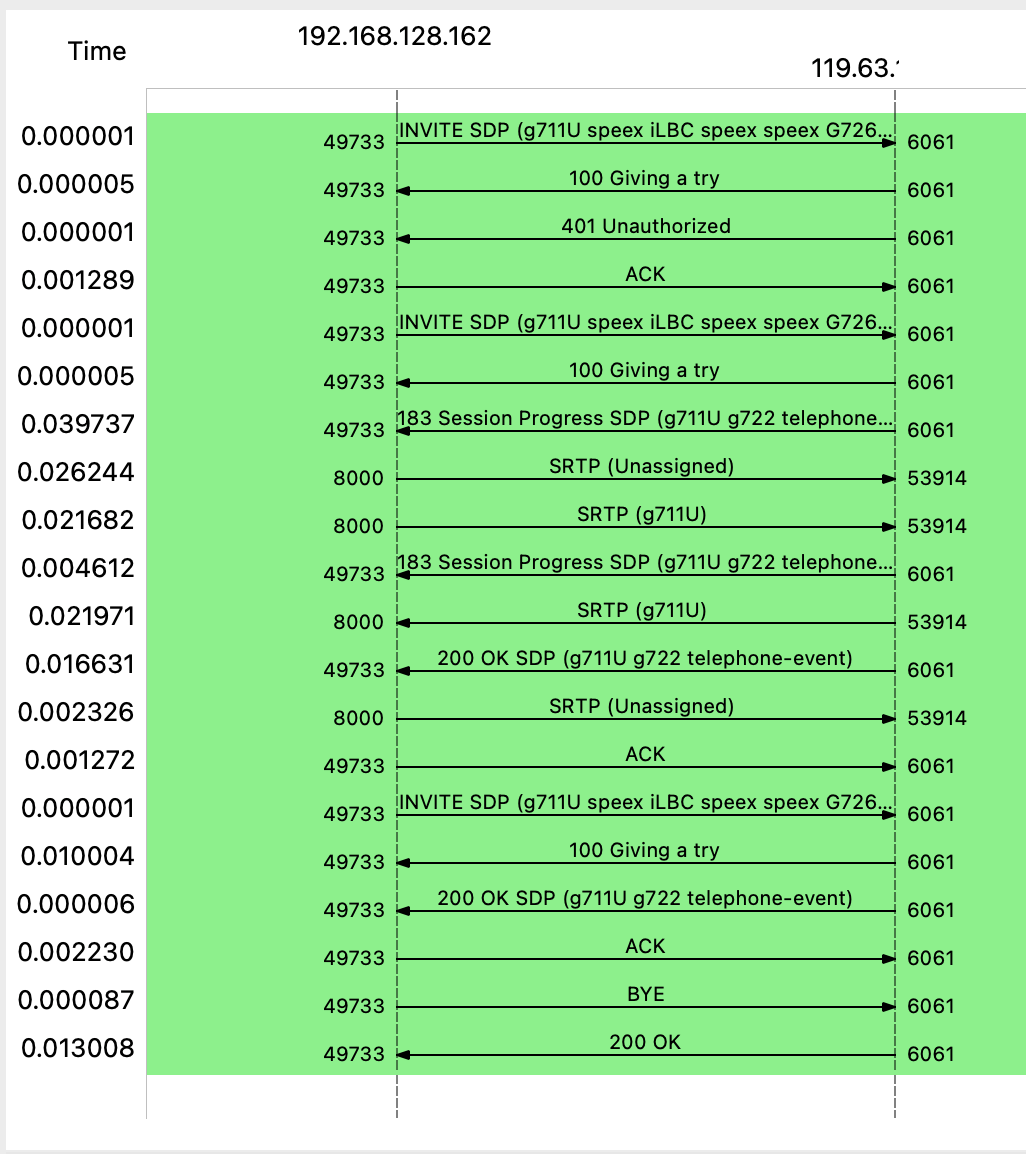
You can see also call flow.